Creating Data Loss Prevention and Data Access Control Policies
Data Loss Prevention (DLP) and Data Access Control (DAC) Policies are custom rules that trigger specific actions when emails are sent or opened. These policies help to protect sensitive data and control access to resources.
This article provides guidance on creating policies and examples of best practices.
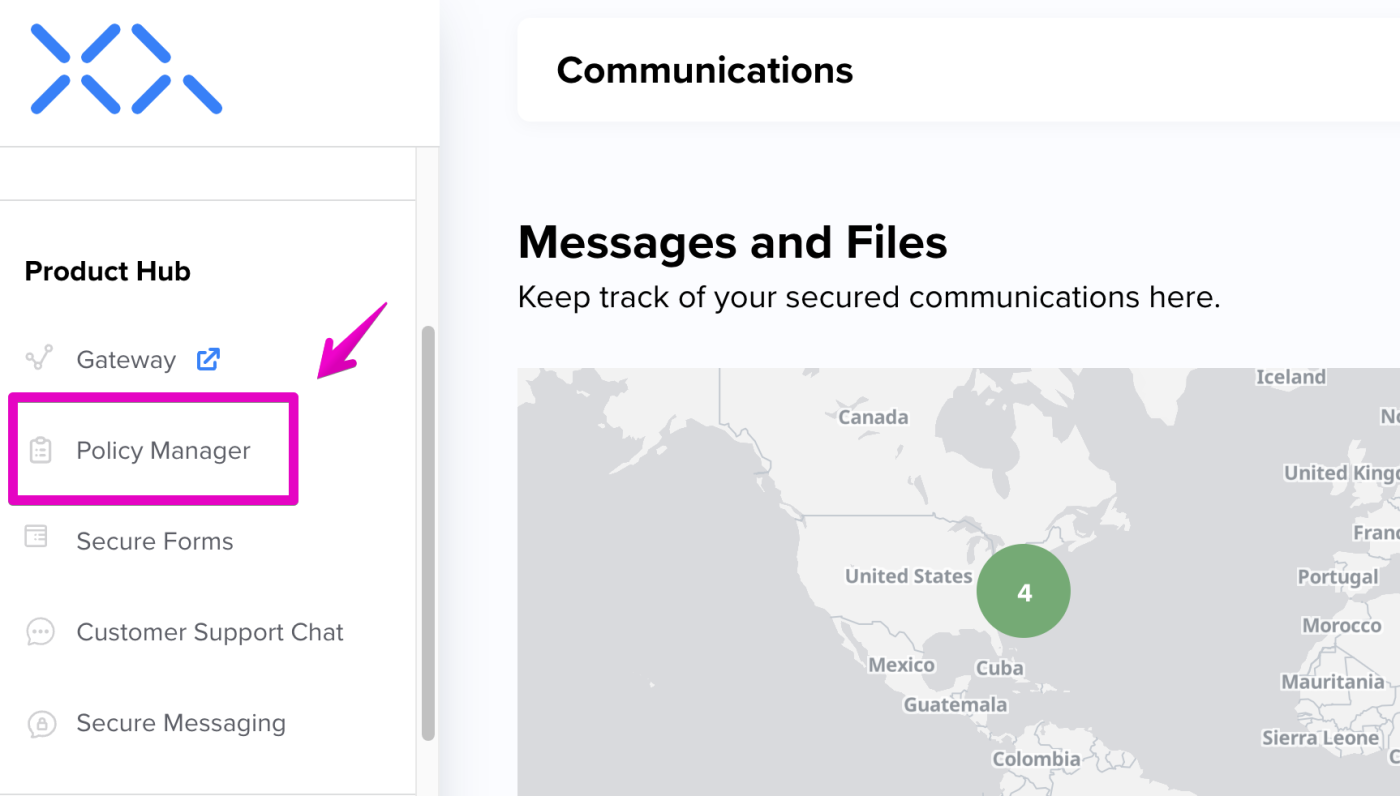
Step 1: In the XQ Dashboard, click Policy Manager in the left-hand navigation bar.
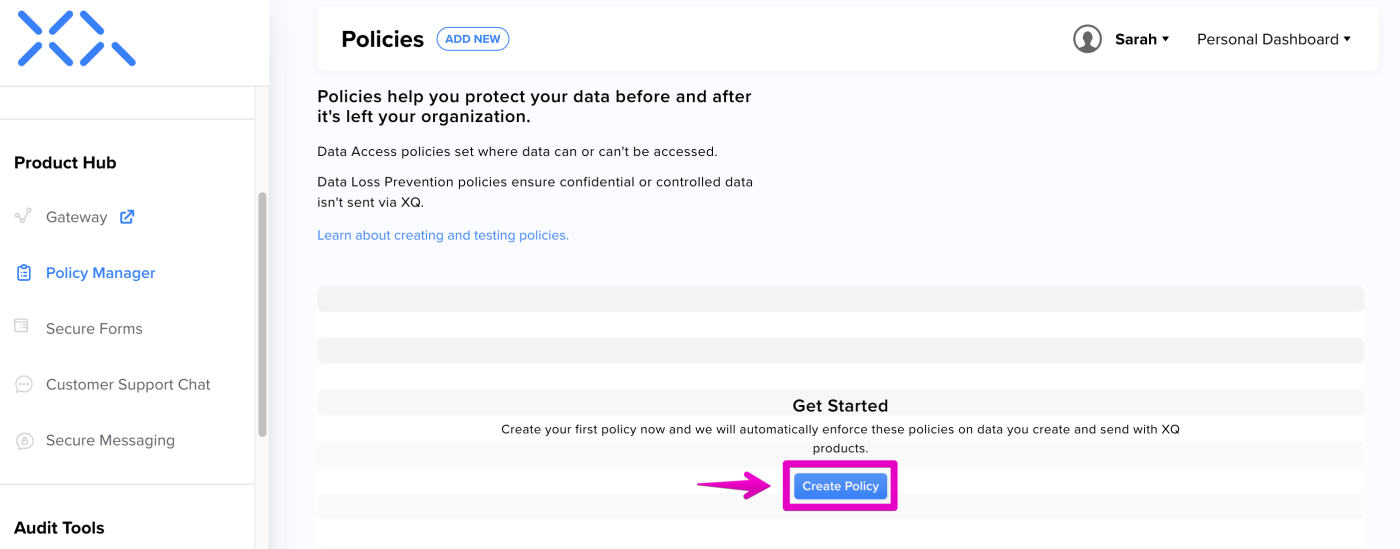
Step 2: Click Create Policy to launch the New Policy page.
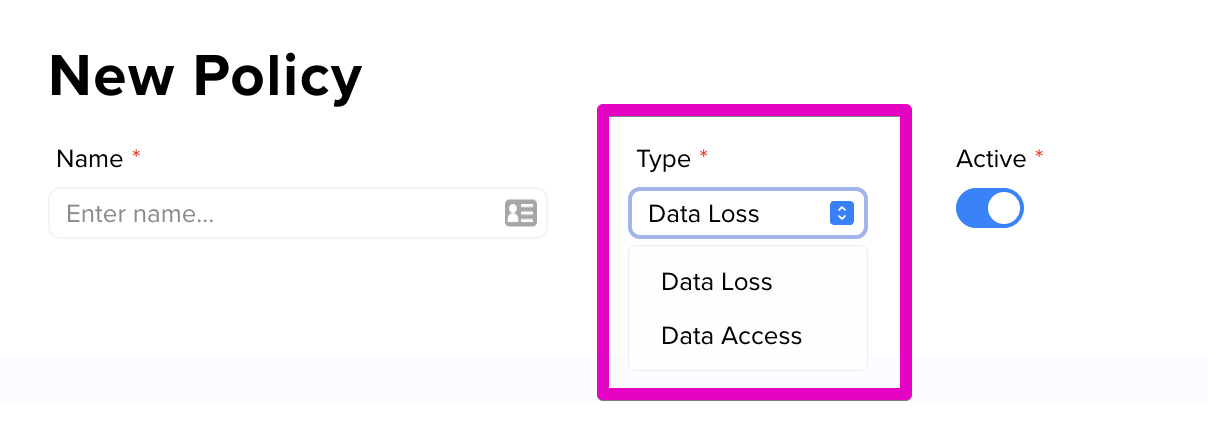
Step 3: On the New Policy page, use the Type drop-down menu to choose your policy type. The available types are Data Loss and Data Access.
Use the following sections in this article to create your Data Loss and Data Access policies.
DLP Policies play a crucial role in meeting CMMC compliance requirements, as they:
Step 1: Launch the Policy Manager in your XQ Dashboard and click Create Policy If you have already created a policy previously, click the ADD NEW button at the top of the page.
Step 2: On the New Policy page, name your policy for future reference and select Data Loss from the Type drop-down.
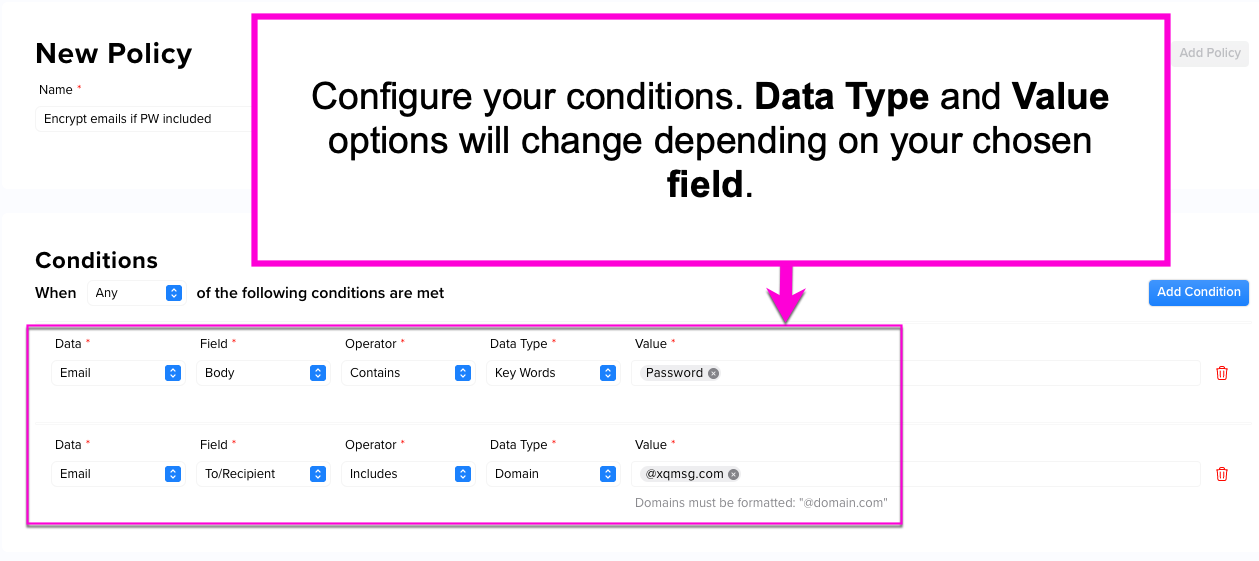
Step 3: Choose your policy's Conditions. Conditions control which criteria must be met to activate your policy. You can choose between these options:
Step 4: Choose whether to Send or Block the message. For example, if you want to prevent team members from sending messages containing specific keywords, select Block.
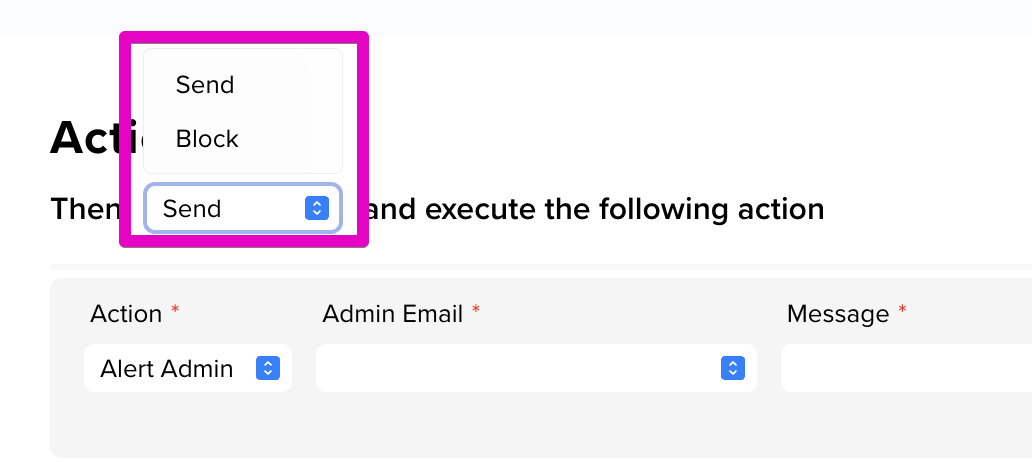
Step 5: Then, choose to execute any of the following actions:
Step 6: Click Add Policy at the top-right corner of the page to save your Data Loss Prevention Policy.
For CMMC compliance, we recommend using the following keywords for your auto-encryption policy:
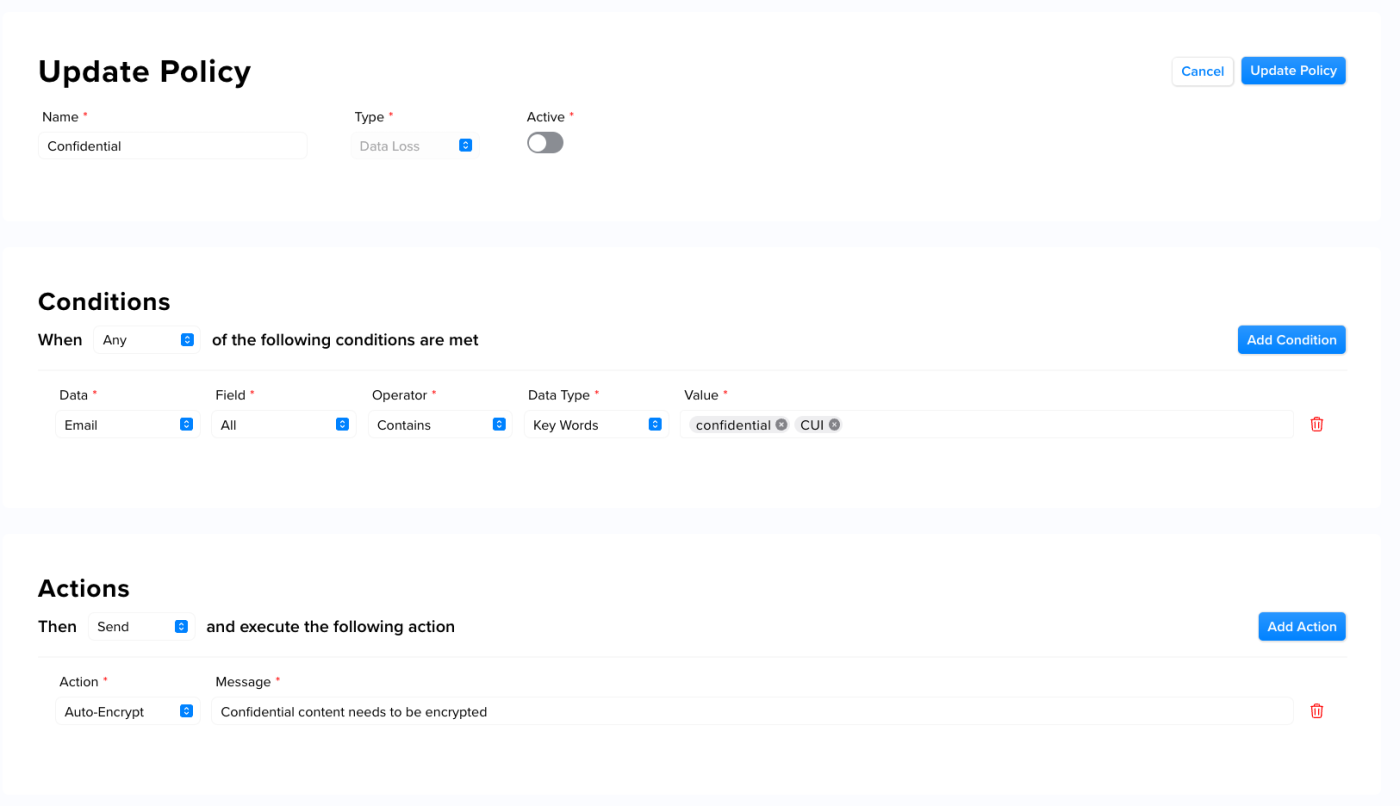
The following example provides an example of an auto-encryption policy that uses keywords:
As an additional measure to ensure the security of sensitive information, we suggest automating the encryption of all email attachments. This guarantees that all attachments are always protected by encryption, regardless of their contents.
DAC Policies play a crucial role in meeting CMMC compliance requirements, as they:
Step 2: On the New Policy page, name your policy for future reference and select Data Access from the Type drop-down.
Step 3: Choose your policy's Conditions. Conditions control which criteria must be met to activate your policy. You can choose between these options:

Step 5: Choose an Action. The available options include:
Step 6: Click Add Policy at the top-right corner of the page to save your Data Access Control Policy.
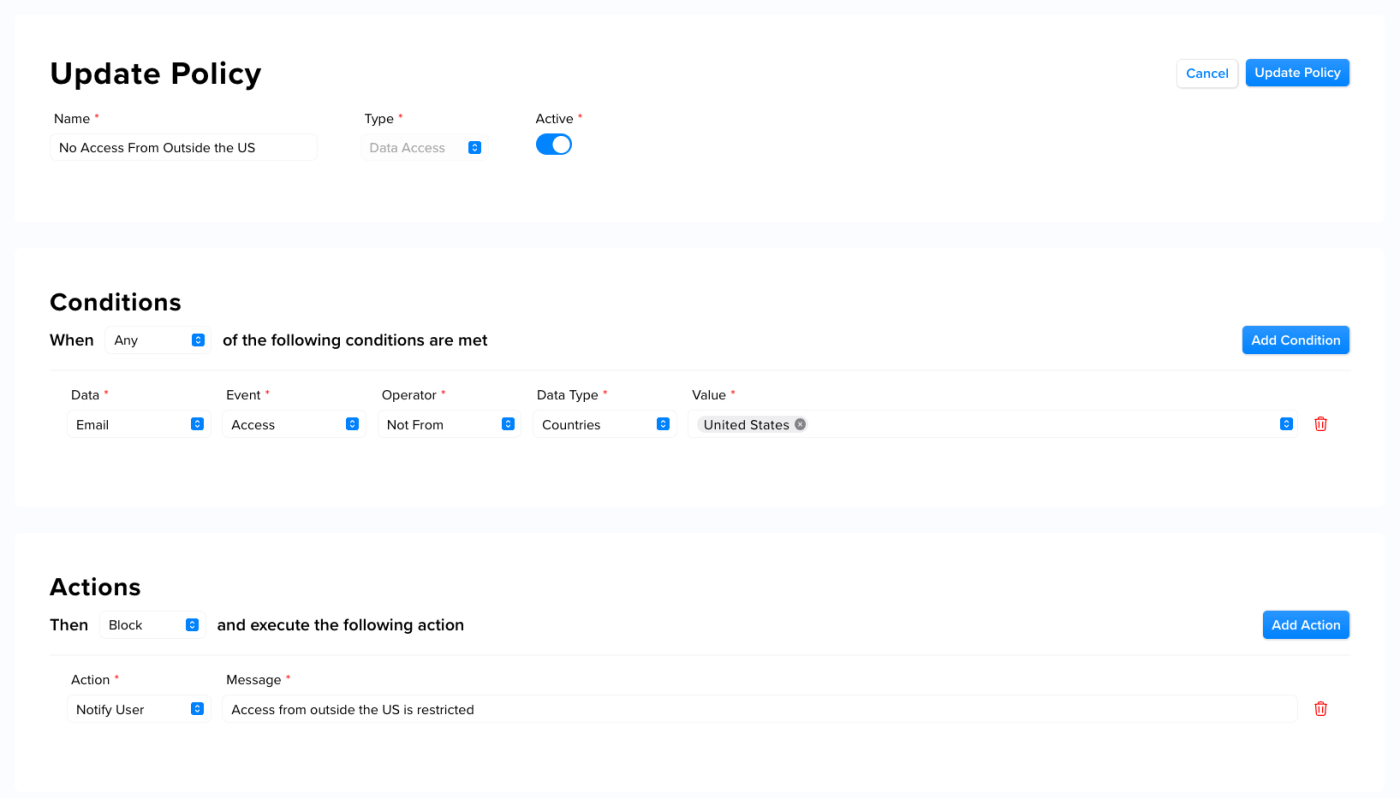
This example shows a location-based restriction policy that restricts data access from outside the United States:
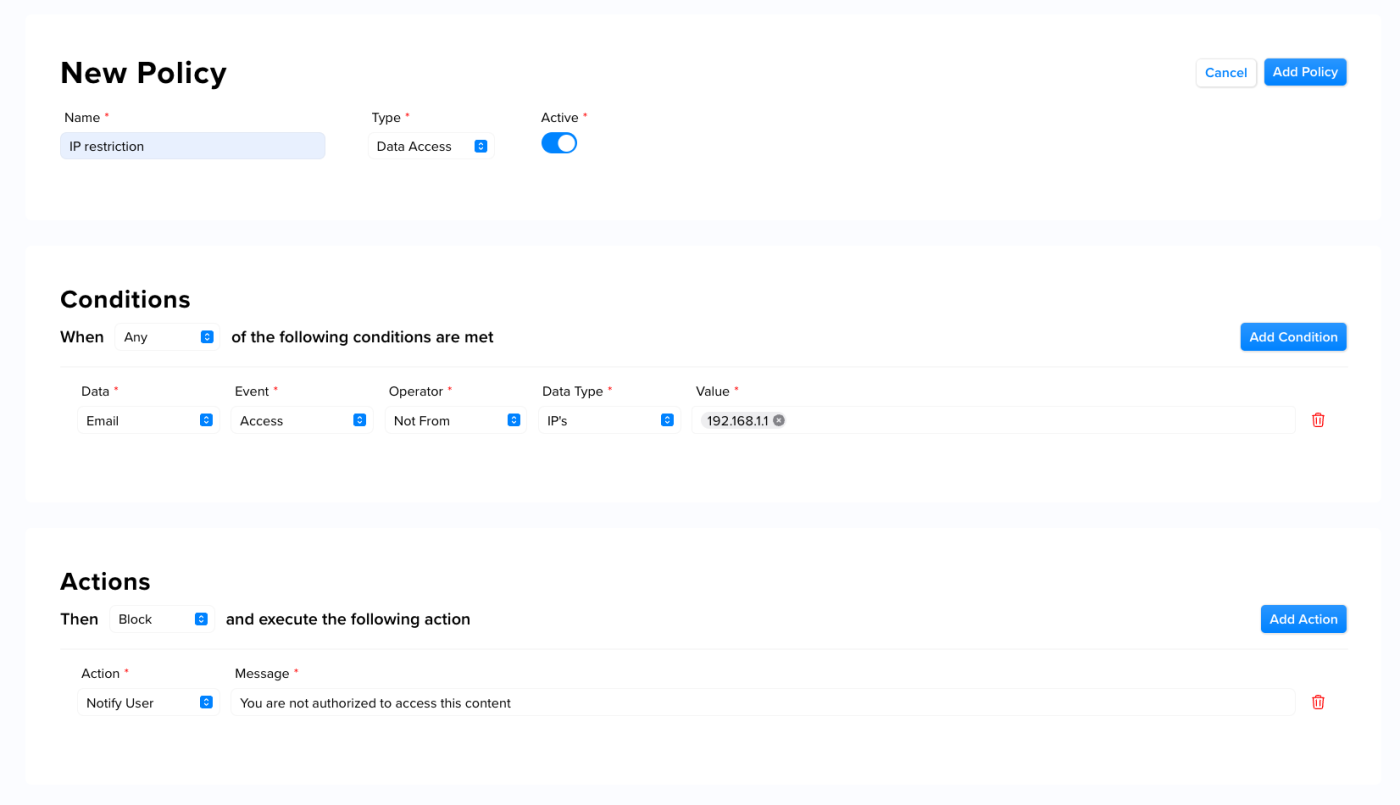
This example shows an IP address-based restriction policy that restricts data access to one authorized IP address:
This article provides guidance on creating policies and examples of best practices.
Note: The examples in this article are best practices. We recommend discussing your DLP and DAC Policies with your CMMC assessor to ensure compliance with NIST 800-171 requirements.
Access the Policy Manager
Using XQ's Policy Manager, you can configure DLP and DAC Policies right from your team's XQ Dashboard. Use the following steps to access the Policy Manager in your dashboard:Step 1: In the XQ Dashboard, click Policy Manager in the left-hand navigation bar.

Step 2: Click Create Policy to launch the New Policy page.

Step 3: On the New Policy page, use the Type drop-down menu to choose your policy type. The available types are Data Loss and Data Access.

Use the following sections in this article to create your Data Loss and Data Access policies.
Creating Data Loss Prevention Policies
Creating Data Loss Prevention (DLP) Policies in XQ ensures the protection of controlled unclassified information (CUI) using automated encryption. With XQ, you can secure your data anywhere it travels.DLP Policies play a crucial role in meeting CMMC compliance requirements, as they:
- Help companies fulfill multiple NIST 800-171 requirements.
- Enable companies to identify the types of data that require encryption.
- Allow companies to create custom profiles and rules for different types of data.
Create a new policy
Use the following steps to create a Data Loss Prevention (DLP) Policy:Step 1: Launch the Policy Manager in your XQ Dashboard and click Create Policy If you have already created a policy previously, click the ADD NEW button at the top of the page.
Step 2: On the New Policy page, name your policy for future reference and select Data Loss from the Type drop-down.
Step 3: Choose your policy's Conditions. Conditions control which criteria must be met to activate your policy. You can choose between these options:
- Data: What body of data is being referenced? For now, you can only choose Email.
- Field: What field is being referenced in your email? You can choose whether to reference a recipient or the contents within the message itself.
- Operator: Select the available operator from the drop-down. The operator works by triggering your policy if the Data Type includes your chosen Value. Operator options change depending on the field you choose.
- Data Type: Choose whether to allow or restrict email access based on your chosen Field. The options will change depending on the field you choose. For example, if your field is To/Recipient, you can choose between Domain and Email Address. If your field is Body, you can choose between Keywords and Pattern.
- Value: Depending on your chosen Data Type, enter a value or select from the dropdown list.

Step 4: Choose whether to Send or Block the message. For example, if you want to prevent team members from sending messages containing specific keywords, select Block.

Step 5: Then, choose to execute any of the following actions:
- Notify User: Notifies the user who created the message. You can customize the message that is sent.
- Log: Log this event in the event log. You can customize the message included in this log.
- Auto-Encrypt: Automatically encrypts the message.
Step 6: Click Add Policy at the top-right corner of the page to save your Data Loss Prevention Policy.
Best practice recommendation: Auto-encryption
To achieve CMMC compliance with Data Loss Prevention (DLP) Policies, we recommend creating auto-encryption policies in XQ. Auto-encryption policies allow you to create criteria using keywords or specific conditions. This eliminates the chance of human error and ensures that all sensitive information is properly encrypted before being sent.For CMMC compliance, we recommend using the following keywords for your auto-encryption policy:
- CUI
- Confidential
- Controlled
- Classified
- FAO
- Invoice
- JADC2
- NDA
The following example provides an example of an auto-encryption policy that uses keywords:

As an additional measure to ensure the security of sensitive information, we suggest automating the encryption of all email attachments. This guarantees that all attachments are always protected by encryption, regardless of their contents.
Creating Data Access Control Policies
Data Access Control (DAC) policies empower the system administrator to set rules for accessing a resource. These rules are established by assigning permissions to designated users. With DAC policies, the administrator can determine who can access the resource and the level of access they are permitted.DAC Policies play a crucial role in meeting CMMC compliance requirements, as they:
- Help companies fulfill multiple NIST 800-171 requirements.
- These policies provide administrators the ability to establish who is authorized to access a resource and the actions they are allowed to perform with it.
Create a new policy
Step 1: Launch the Policy Manager in your XQ Dashboard and click Create Policy If you have already created a policy previously, click the ADD NEW button at the top of the page.Step 2: On the New Policy page, name your policy for future reference and select Data Access from the Type drop-down.
Step 3: Choose your policy's Conditions. Conditions control which criteria must be met to activate your policy. You can choose between these options:
- Data: What body of data is being referenced? For now, you can only choose Email.
- Event: What event is happening to your email? For now, you can only choose Access.
- Operator: Choose to trigger your policy if the Data Type is From or Not From a country or IP address.
- Data Type: Choose whether you're allowing or restricting email access based on countries or IPs.
- Value: Depending on your chosen Data Type, select a country or input an IP address.

Step 5: Choose an Action. The available options include:
- Alert Admin: This action sends a customized email to a specific admin. Optionally, you can include '$User' in your message to display the email address of any user attempting to send a message affected by your policy (eg. $USER tried sending a message with the word 'password' included).
- Notify User: This action notifies the user who created the message. You can customize the message that is sent.
- Log: This action logs this event in the event log. You can customize the message included in this log.
Step 6: Click Add Policy at the top-right corner of the page to save your Data Access Control Policy.
Best practice recommendation: Location-based restriction
Location-based restriction policies enable you to limit access to resources based on geographical location. These policies prevent unauthorized individuals located outside the designated geographical location from accessing the resource.This example shows a location-based restriction policy that restricts data access from outside the United States:

Best practice recommendation: IP address restriction
Further limiting access through IP address restrictions provides a more secure way of controlling user access. When implementing this type of policy, specific IP addresses are designated as authorized for accessing a resource. Attempts to access data from an unapproved IP address will be blocked.This example shows an IP address-based restriction policy that restricts data access to one authorized IP address:

Tagged: